Cryptocurrency beginners must comprehend public and private keys. These keys protect cryptocurrency transactions and access.
It is absolutely necessary for anyone just starting out in the crypto sector to have a solid understanding of what public keys and private keys are as well as the purposes they serve.
What are public and private keys in the field of cryptography?
The first step in entering the realm of cryptocurrency is creating a wallet. You begin working with public keys and private keys at this point. What are they, though?
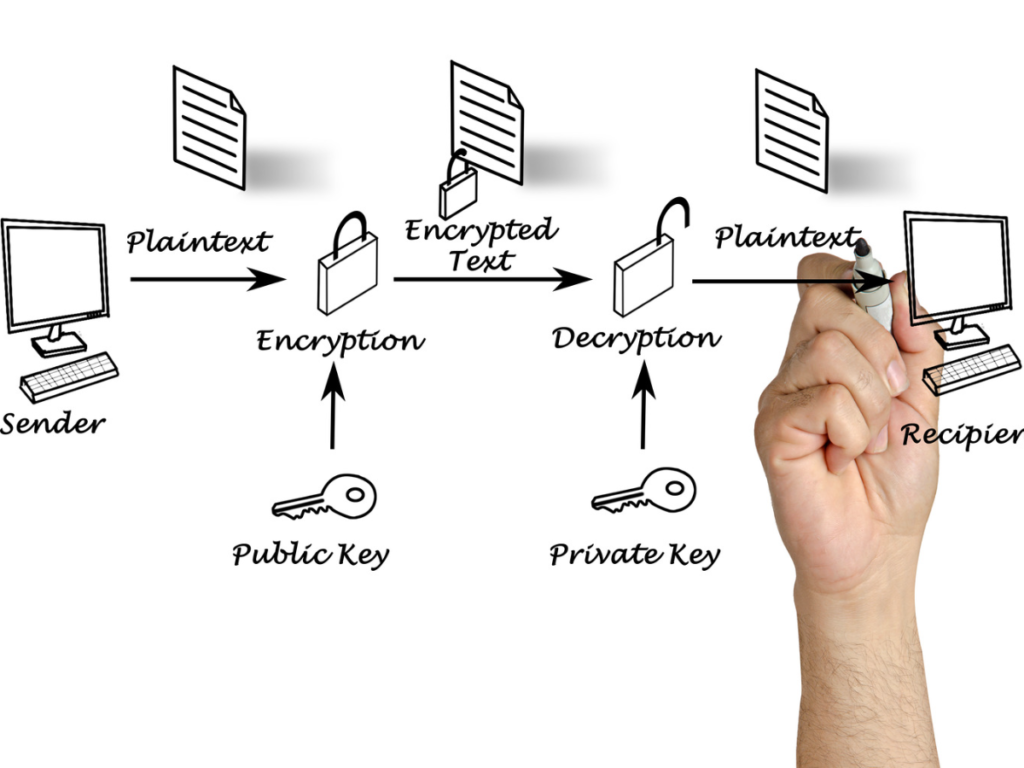
The private key is used to send cryptocurrency transactions, while the public key is an encrypted code coupled with it. While anyone can send transactions to the public key, only the owner of the cryptocurrency that was received in the transaction can “unlock” such transactions and show they were sent by them.
Typically, a wallet address—a 42-character string provided by the recipient to receive cryptocurrency—serves as the public key that can receive transactions. The wallet address serves as the IBAN of a particular cryptocurrency’s account and is just a condensed version of the public key.
In general, sharing one’s public key is quite safe. The private key, on the other hand, is only intended for the wallet’s owner and needs to be kept a secret.
In reality, a bitcoin wallet’s private key serves as a password in the cryptosphere. In the unlikely event that this password is ever misplaced or stolen, whoever has it has access to the wallet and is free to do anything they want with the crypto assets they discover.
Private keys are specifically numerical codes, which can be encoded as 256-character binary, 64-digit hexadecimal, QR, or even mnemonic phrases.
Several crypto-wallets contain public and private keys
Speaking of private keys, it’s critical to understand how the crypto-wallet you’ve chosen to use to store your coins operates.
The private key is encrypted by several crypto wallet providers in a way that makes it simpler to store and recall.
A “seed phrase,” also referred to as a “secret recovery phrase,” is used by some wallets to open the wallet. If you select the non-custodial cryptocurrency wallet offered by MetaMask, the user will be given a set of random phrases to use to unlock the funds. Underneath this user-friendly string of words, the private key is concealed within the software.
In contrast, if you select a wallet from a centralized platform like Binance or Coinbase, the business will keep the user’s private key on their behalf. In this way, the wallet service provider manages the user’s money.
Cryptographic transactions are digitally signed using both public and private keys
The main function of these public and private keys is to sign cryptographic transactions. To confirm the legitimacy of the transaction on the relevant Blockchain, this digital signature is used.
The steps in a transaction on the Blockchain are as follows:
- A public key is utilized to encrypt a transaction. Only the private key that is included in the transaction can be used to decrypt it;
- The transaction is then signed using the private key, demonstrating that it has not been altered. The private key and the transaction’s data are combined to create the digital signature;
- With the included public key, it is possible to confirm the transaction’s legitimacy.
In order to demonstrate that they are the rightful owners of the funds, the user digitally signs a transaction. Nodes automatically verify and authenticate transactions. The network rejects any transaction that is not authenticated. On the blockchain, a transaction that has been verified and mined is irreversible.
The IronKey and Stefan Thomas’s narrative
The cryptographic community is fundamentally based on public and private keys. This is demonstrated by the story of Stefan Thomas and his IronKey.
Thomas, a computer developer, could lose 220 million Bitcoin because he lost the password to his IronKey encrypted storage device, where he saved his wallet private keys.
The developer cannot access his wallets because his IronKey stores everything. Even he can’t remember his password, therefore it’s safe.
Paradoxically, the IronKey only permits the user to input a password 10 times until it is no longer accessible. By the time the tale was told, Thomas had already made eight unsuccessful attempts to log in.
According to this tale, storing private keys on IronKey is likewise not a suitable option. Instead, it is intended to maintain the seed phrase or private key written down on paper so that at least its owner can quickly access it.